Due to the success of Microsoft Teams, the question of which data / whether sensitive data can be stored and processed in Office 365 is being asked more and more. This can be triggered by aspects of the GDPR as well as company- or industry-specific compliance rules. With the Sensitivity Labels, Microsoft Information Protection provides an option for labeling and additionally encrypting content. This is generally an option for storing and processing sensitive data in the cloud. The feature is included in the Office 365 E3 license and higher. However, only manual labeling is available in the Office 365 E3 license.

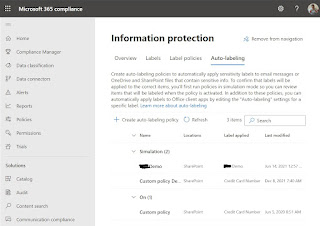
For example, to implement the following requirement, at least a license is needed that includes the Auto-Labeling feature: "All files stored in the Management Team should automatically be labeled as Internal Onyl." This is possible using the Office 365 E5 license or a license add-on such as Microsoft 365 E5 Security & Compliance. With this license, the Auto-Labeling feature in the Microsoft 365 Compliance Center will also be available:
This allows content in Exchange, SharePoint and OneDrive to be automatically labeled based on rules:
However, this only applies to Office files of type Word (.docx), PowerPoint (.pptx), and Excel (.xlsx) in SharePoint and OneDrive. For Exchange Online, PDF attachments and Office files are checked against the conditions in the Auto-Labeling Policy. If there is a match, the email is labeled, but not the attachment. Details:
Apply a sensitivity label to content automatically
Automatic labeling of non-Office files
Sensitive content is often also contained in non-office files. First and foremost, the PDF format is relevant, followed by formats such as *.jpg, *.png or Visio files (*.vsdx) etc. The complete list of formats supported by Microsoft Information Protection is listed in this article:
Supported file types for classification and protectionThese
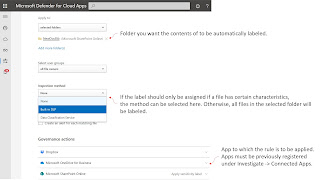
filetypes can also be automatically labeled. For this scenario, a file policy
is created in Defender for Cloud Apps:
Protect other file types
When you need to encrypt files that are not included in the list of supported file types for classification and protection, you can use the Information Protection Client.
The client can encrypt and decrypt any file format. However, if the format is not on the list of supported file types, the Information Protection Viewer cannot be used to show the file. The file has to be saved decrypted before it can be opened with the native client app. This is currently still the case for video formats, for example.
A way to protect such files by automatic labeling is shown in the following example:
- Synchronize the folder with the video files to be encrypted with OneDrive for Business.
- Encrypt the video files locally via script: Set-AIPFileLabel -Path C:\Project Videos\ -LabelId d9f23ae3-1324-1234-1234-f515f824c57b
- OneDrive for Business then synchronizes the encrypted video files back to SharePoint Online
Microsoft has now announced a new feature that provides a similar result. This allows a SharePoint Online document library to be assigned a label that is then automatically applied to all files in this library.
https://www.microsoft.com/en-us/microsoft-365/roadmap?filters=&searchterms=85621