Using Azure AD to provide access to resources in another tenant is not new. The Azure B2C and B2B feature have been available for several years. Now Microsoft has released the Cross-Tenant Access Settings feature as Preview. This allows general settings and settings per tenant, which is accessed as a guest user or from which guests access your own environment:
In addition, there is the option to accept the multifactor authentication that may already have been performed when logging on to the other Azure AD. Another option relates to the status of the device used, which can then be verified in a conditional access policy, for example. Both the "Compliant Device" status and the "Hybrid Azure AD Joined" status can be trusted:
Overview Cross-tenant access with Azure AD External Identities
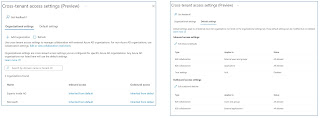
Using Cross-tenant access settings you can set default settings for your environment as well as settings per tenant from which accesses are made. So if you work with partners or selected customers on a regular basis, you can configure explicit rules for B2B collaboration - External users and groups, B2B - collaboration Applications and Trust settings for inbound and outbound traffic:
The following applies:
- The default settings apply to all external Azure AD's that are not listed in the Organizational Setting tab. These default settings can be changed, but not deleted.
- For access that is not authenticated via an Azure AD, the settings under: Edit or view collaboration restrictions applys
Configure cross-tenant access settings
The default settings for inbound and outbound traffic can be set to B2B collaboration - External users and groups, B2B - collaboration Applications and Trust settings. These values then apply to all tenants that are not explicitly registered:
On the Organizational Setting tab, explicit environments can be added via Add Organization:
These can then either also inherit the default settings, or get explicit settings:
The following settings can be configured for each tenant:
- Select explicit external users and groups:
- Select applications:
- Settings for MFA and device
Source and more details: Configure cross-tenant access settings for B2B collaboration
Reporitng
Reports on access from other tenants can be created both via PowerShell and via the "Monitoring" tab in Azure AD.
Example via PowerShell for cross-tenant sign-in activity:
- Get-MSIDCrossTenantAccessActivity -SummaryStats -ResolveTenantId
Get-MgAuditLogSignIn `
-Filter “ResourceTenantID ne ‘your tenant id’” `
-all:$True| `
group ResourceTenantId,AppDisplayName,UserPrincipalName| `
select count, @{n=’Ext TenantID/App User Pair’;e={$_.name}}]
Source and more details: Identify inbound and outbound sign-ins
Cross-tenant access activity workbook:
This workbook is available in the Azure AD under "Monitoring" and provides reports that can be filtered by the following values:
- Time range (up to 90 days)
- External tenant ID
- User principal name
- Application
- Status of the sign-in (success or failure)









Keine Kommentare:
Kommentar veröffentlichen