Microsoft Sentinel can be used via the Microsoft Teams workbook or the Office 365 workbook to monitor Teams. The integration is done via the Data Types OfficeActivity respectively via the logs of Microsoft Teams in M365.
In the Microsoft Sentinel Content Hub, the template "Microsoft Sentinel for Teams" is now also available as a preview. The template installs 2 Analytics Rule, 7 Hunting Query and 2 Playbooks with which Teams can be monitored and the logs can be filtered for threats.
The installation is dialog-driven and quite simple. When the deployment has been successfully completed, the following page is displayed with an overview of what was installed.
What is deployed?
Analytics
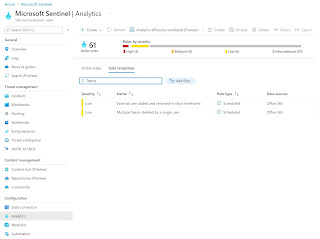
Analytics Rules are used to create rules for threat detection. The template creates two rules for Microsoft Teams:
- External user added and removed in short timeframe: This rule flags when external users are added to a Team and then removed within an hour.
- Multiple Teams deleted by a single user: This rule indicates when multiple Teams are deleted within one hour.
These analysis rules are created in disabled mode and can be enabled / customized in the analysis rules gallery in Sentinel:
Hunting Queries
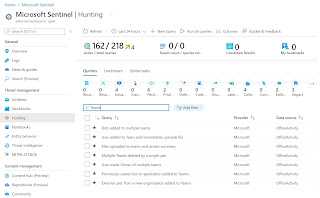
Microsoft Sentinel provides queries to search for threats in the connected data sources. This enables targeted searches for suspicious behavior or unusual activity. The template installs the following hunting queries with a focus on Microsoft Teams:
- External user from a new organization added to Teams: This query identifies external users that have been added to Teams, where the user's domain has not yet been used.
- Multiple Teams deleted by a single user: This query shows when multiple Teams have been deleted by a single user within a short period of time.
- Bots added to multiple Teams: This query helps identify bots that have been added to multiple Teams in a short period of time.
- User made owner of multiple Teams: This identifies users who have been made owners of multiple Teams.
- Previously unseen bot or application added to Teams: New and possibly unapproved applications or bots added to Teams are identified with this query.
- Files uploaded to Teams and access summary: This query shows files uploaded to SharePoint via a Teams chat and summarizes the users and IP addresses that accessed those files. This allows for the identification of anomalous file sharing patterns.
- User added to Team and immediately uploads file: This identifies users who have been added to a Team or Chat and uploaded a file via Chat within one minute of being added. This could be an indicator of suspicious activity.
Playbooks
Playbooks are a collection of procedures that can be executed in response to an alert or incident. A playbook can be used to automate actions when certain warnings or incidents are detected.
A sticking point in the "Playbook" setup step, as seen in the screenshot, is that a user must be added here who has the right to connect to the Teams API.
To do this, this user must be given consent. A simple way to do this is described here: https://docs.microsoft.com/en-us/graph/auth-v2-user#consent-experience The user that you want to use logs in and grants consent. The fact that the link to which you are then redirected is empty is irrelevant.






Infrassist Technologies Pvt. Ltd. is a Master MSP (IT Service Providers) based in India. We have partnered with and served 75+ MSPs across 15+ Countries. If you want to avail our services, visit our website
AntwortenLöschenProfessional Services
Microsoft 365
IT Automation Services
rmm solutions
Firewall Audit
IT Infrastructure Management
Office admin
Azure admin
rmm audit
Firewall audit
Support Services
Noc Services
Helpdesk