This blog is about Microsoft technologies and solutions. The focus is on Microsoft 365, Office 365, Azure, Collaboration, Security and Compliance topics.
Sonntag, 27. März 2022
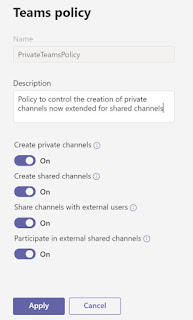
Microsoft Teams Shared Channels
Donnerstag, 24. Februar 2022
Graph Insights Adjustments
- Profile Cards
- User Profile in Delve
- Listing relevant people / working with overview
Customize Insights
Customize PeopleInsights
- Disable PeopleInsights for all users:
PATCH, beta:{"isEnabledInOrganization": false}
- Disable PeopleInsights for an Azure AD Group by additionally using the disabledForGroup paramter:
PATCH, beta:{"isEnabledInOrganization": false,"disabledForGroup": "f742839d-2321479-4de9-9616-e61877675c88c"}
To do this, for example, with Microsoft Graph Explorer, the following steps are performed:
- Open Graph Explorer and log in: https://developer.microsoft.com/en-us/graph/graph-explorer
- GET, beta: https://graph.microsoft.com/beta/organization returns the OrganizationId that is needed in the next step:
- Get the current settings:
GET, beta: https://graph.microsoft.com/beta/organization/{organizationId}/settings/peopleInsights
- Customize the settings as needed:
PATCH, beta:{"isEnabledInOrganization": false,"disabledForGroup": "f953948d-3423-4ac7-9616-d6187975c00c"}
- The settings for PeopleInsights are currently only available in BETA.
- The update process does not check if an Azure AD Group exists. If the Group does not exist, no changes will be made for any user.
- It can take up to 24 hours for insightsSettings adjustments to take effect, or longer in the BETA version.
Montag, 21. Februar 2022
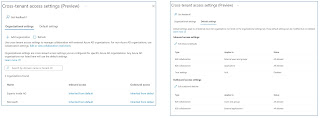
Cross-tenant access settings in Azure AD
In addition, there is the option to accept the multifactor authentication that may already have been performed when logging on to the other Azure AD. Another option relates to the status of the device used, which can then be verified in a conditional access policy, for example. Both the "Compliant Device" status and the "Hybrid Azure AD Joined" status can be trusted:
Overview Cross-tenant access with Azure AD External Identities
- The default settings apply to all external Azure AD's that are not listed in the Organizational Setting tab. These default settings can be changed, but not deleted.
- For access that is not authenticated via an Azure AD, the settings under: Edit or view collaboration restrictions applys
Configure cross-tenant access settings
- Select explicit external users and groups:
- Select applications:
- Settings for MFA and device
Reporitng
- Get-MSIDCrossTenantAccessActivity -SummaryStats -ResolveTenantId
Get-MgAuditLogSignIn `
-Filter “ResourceTenantID ne ‘your tenant id’” `
-all:$True| `
group ResourceTenantId,AppDisplayName,UserPrincipalName| `
select count, @{n=’Ext TenantID/App User Pair’;e={$_.name}}]
- Time range (up to 90 days)
- External tenant ID
- User principal name
- Application
- Status of the sign-in (success or failure)
Dienstag, 15. Februar 2022
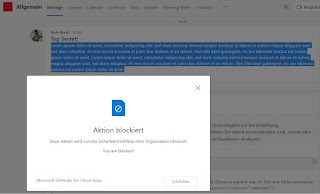
Restrict Microsoft Teams Copy & Paste
For example, it can prevent users from copying content from Teams chats and posting it in other apps. In general, it is important to consider whether these restrictions apply to the web version of Microsoft Teams or to the Teams client/app. Both can be restricted, but different solutions are used in each case:
Restrict copy & paste when accessing via the browser
- Send item
- Send Teams message
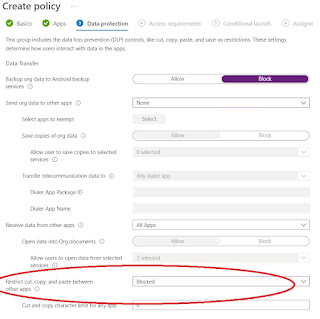
Restrict copy & paste when accessing via Teams client / Teams app
- Backup org data to Android backup services
- Send org data to other apps
- Receive data from other apps
- Screen capture
- Printing org data
- Restrict web content transfer with other apps
Mittwoch, 15. Dezember 2021
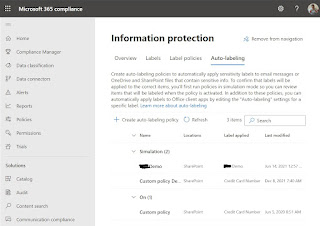
Automatically encrypt content in Office 365 services
Automatic labeling of non-Office files
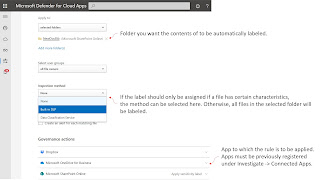
Protect other file types
- Synchronize the folder with the video files to be encrypted with OneDrive for Business.
- Encrypt the video files locally via script: Set-AIPFileLabel -Path C:\Project Videos\ -LabelId d9f23ae3-1324-1234-1234-f515f824c57b
- OneDrive for Business then synchronizes the encrypted video files back to SharePoint Online
Freitag, 26. November 2021
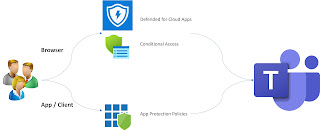
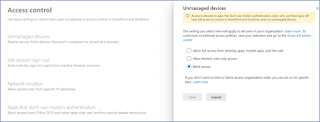
Step by Step guide - limit access to Teams
Step by Step guide & scenarios to limit access to Teams (SharePoint, Exchange, etc.) from an unmanaged device.
- Access to teams should only be possible via the browser, which has the advantage that no local log files etc. are written or data is not stored in a local device backup. This is especially important for mobile devices (iOS, Android), as these backups may be stored in further cloud services.
- Download of files should not be possible. Accessing and editing in the browser shall be possible.
- Download, access and editing of files should not be possible.
Solution
- App Restriction (SharePoint & EXO Admin Center)
- Azure AD Conditional Access
- Conditional Access App Control, as described here: Use app enforced restrictions vs. Use Conditional Access App Control
- Authentication Context, as described here: Azure AD Conditional Access | Authentication Context
Step by step guide on the example
Tips & Tricks
- It can take several minutes for a Conditional Access policy to take effect / for a change to take effect.
- For tests in which policies are changed, the following applies: Always log off, close browser / clear browser cache, wait several minutes and then log in again.
Samstag, 30. Oktober 2021
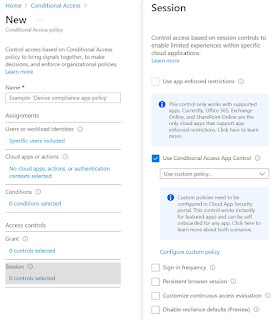
Azure AD Conditional Access | Authentication Context
The Authentication Context feature can be used to add additional and granular security to access apps or data in apps such as SharePoint or Exchange.
Example: Access to SharePoint sites or data in SharePoint is only permitted with devices managed in Intune. This is enforced via a conditional access policy. For special SharePoint sites containing highly sensitive data, access is also only permitted from the company network.
Until now, this was not possible because a conditional access policy always referred to the app as such, i.e. to SharePoint in the example above. With the Authentication Context in a Conditional Access Policy, this scenario is now possible.
Authentication Context
The feature is still in preview. The following limitations apply to the preview:
- Deleting authentication context definitions is not possible in the preview.
- The preview is limited to a total of 25 authentication context definitions.
An Authentication Context is created in the Conditional Access menu in the Azure Portal: